How to Implement Multi-Factor Authentication in an App?
Written by Hemendra Singh on June 13, 2018 | Updated on: June 13, 2018

Multi-Factor Authentication is the necessity of each business that works with confidential information, i.e., clients’ data. The framework receives a layered approach to security which makes it troublesome for people to access the information. Giving an additional level of security like the password is not enough. Multifaceted Confirmation Framework has turned into the must-have feature of applications. That is the one that deals with payments. Those applications identified with survey or withdrawal of information from the cloud.
Table of Contents
What is Multifaceted Validation Framework or Multi-Factor Authentication(MFA)?
Multifaceted verification or Multi-Factor Authentication(MFA), as we usually call it, works around giving an additional layer of security. It guarantees that clients are giving more than a single bit of proof for their identity. It more often than not requires a mix of something which client knows. That is similar to pins, passwords, something which the client has. It can be same as cards, telephone, or something like unique mark or Retina examine.
There are four different ways through which you can incorporate MFA in your Application. One crucial thing for mobile app development companies to consider. Let us go through every one of them as far as the procedure is concerned.
So, what are the sorts of multi-factor advances?
Equipment tokens:
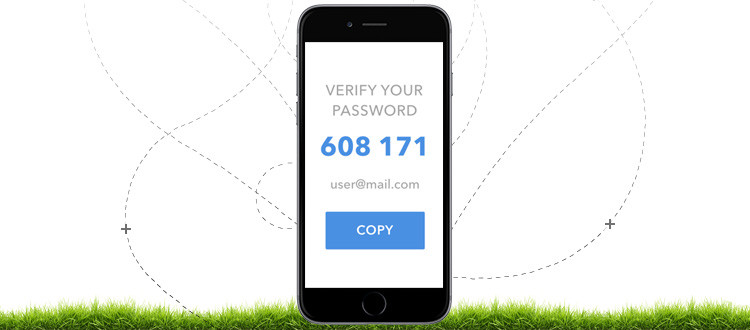
Simple to utilize equipment gadgets that a proprietor carries to approve access to a system. These are robust validation with one-time passwords (OTPs). These equipment tokens give the ownership factor to multi-factor verification. They empower upgraded security for banks and application suppliers. One who need to secure various applications with a single gadget.
OTP contains the production of a one-time password from shared mystery key which accompanies the present timestamp. That to help assistance of correct kind of cryptographic capacity. OTP includes the enlistment and login forms.
Few are the details on both the procedures –
Enlistment Process:
- Clients sign in the application with their passwords and username
- Once you discover the accreditations, the next stage is to empower the two-factor verification
- The shared key is then asked for, which can be either message based or QR code
- The key is put away by an application which executes OTP like Auth0 Guardian or Google Authenticator.
- The two-factor validation is then empowered.
Following is the Login procedure:
- Client sign into the application
- On the off chance that their accreditations are legitimate, they are coordinated to a frame where they need to invest one energy code created with Auth0 Watchman or Google Authenticator.
- The server at that point confirms that the code is legitimate and verifies the client.
Delicate tokens:
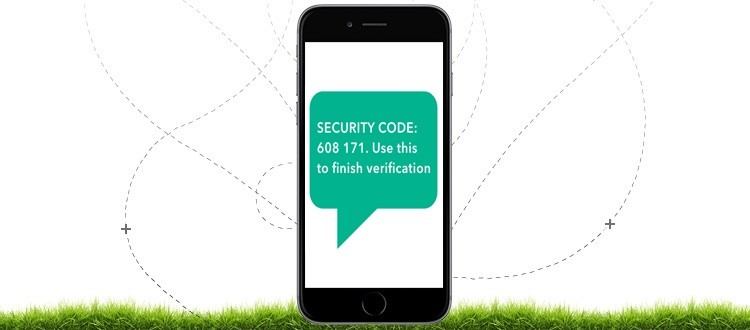
Programming or “application based tokens” produce a one-time login or a PIN. These tokens use multi-factor confirmation. Where the gadget, for this situation a cell phone, gives the ownership factor. The procedure of multifaceted application through SMS includes enlistment and the login.
Enlistment Process:
- Client sign in an application with username and secret key.
- They are requested to enter a telephone number that is working.
- A unique one-time code is then created on an application server and is sent to the client’s telephone number.
- They at that point enter the code in an application, along these lines empowering multifaceted validation.
Procedure to Login:
- Client sign in the application with their client id and secret key.
- A particular one-time code is then produced on an application server and is sent to client’s cell phone number.
- The client enters the code in an application.
- If that discovered is substantial, a client gets validated, and the session gets started.
Mobile confirmation:
Mobile verification is the procedure of checking a client using their device. It involves checking the gadget itself. Thereby enabling clients to sign into secure areas and assets from anyplace with upgraded security.
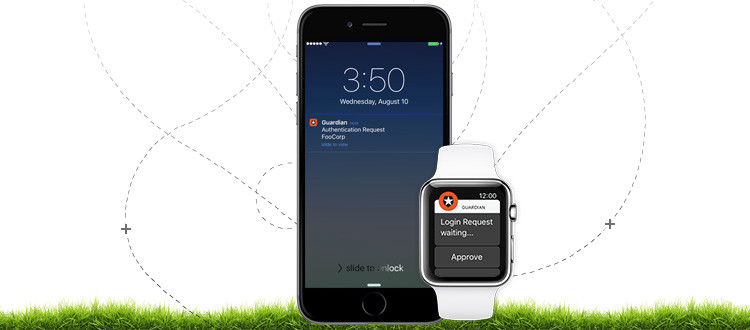
How Pop-up messages Function?
The procedure for an ordinary multifaceted application is the same. The uses of the pop-up message are as per the following:
- A client sign into a site/application with a username and password.
- Push warnings work with applications, for example, Auth0 Gatekeeper. A message pop-up is sent to the Gatekeeper application on your cell phone. This notice is login ask.
- It incorporates data, for example, the application name, the OS and program of the demand, the area and the date of the demand.
The client acknowledges the demand and progresses toward becoming signed-in.
Biometric confirmation:
It incorporates utilizing a unique finger impression sweep or face acknowledgement which is made with the motive to validate clients. Even on cell phones, it conducts verification which gives an undetectable layer of security. It verifies end clients by the one of a kind ways they collaborate with their PC or cell phone. That is through a keystroke, swipe design, mouse development and few others.
How Does E-Mail Process work?
The procedure for a run of the multifaceted mill application utilizing email is as per the following:
- A client sign into a site/application with a username and secret code.
- A one of a kind one-time code is produced on the server and sent through email to the client.
- The client recovers the code from the email and enters the code into the application.
- If it’s substantial, the client is verified, and a session starts.
Incorporating the framework in your application is hard. That too without the Application Improvement Organization. They use some expertise in giving full quality confirmation regarding versatile application security. While this is from the business front, each additional security layer accompanies more work. That too for the clients. It can prompt disappointment when clients are made to rehash various processes. That each time they need to complete a job. The difficulties that the framework accompanies are insignificant. If you compare the advantages that they bring to the table. It is regarding giving the clients a sheltered environment, in the midst of the taking off information break occurrences.
Considering taking your Application Security to the following level? You can Contact our Team of Mobility Experts, today.
My name is Hemendra Singh. I am Managing Director and co-founder of PuzzleInnovationz, a Mobile App Development Company. I am having a keen interest in the latest trends and technologies that are emerging in different domains. Being an entrepreneur in the field of IT sector, it becomes my responsibility to aid my audience with the knowledge of latest trends in the market.

![Oracle Database Advantages, Disadvantages and Features [Guide 2021]](../wp-content/uploads/2019/08/Oracle-Database-Advantages-Disadvantages-150x150.jpg)











